Overview
Amazon Web Services (AWS) is an Amazon subsidiary that provides on-demand cloud computing platforms. AWS hosts numerous products and services, including the Aurora relational database, the Redshift data warehouse product, and the Simple Storage Service (S3).
Amazon S3
Amazon S3 (Simple Storage Service) is a cloud computing data service offering from Amazon Web Services (AWS). Amazon S3 provides storage through web services interfaces.
Accessing S3 buckets
Data Management can access S3 resources in two ways:
-
Bucket policies grant access when the request originates from approved IP addresses or Amazon Virtual Private Cloud (Amazon VPC) endpoints.
Your AWS administrator must configure the S3 buckets to ensure that the servers running Data Management have access to the desired buckets.
-
Account-based access, where access is granted when the correct credentials are presented and authenticated. This may happen automatically via the default credential provider chain if the credentials are present on the Data Management servers either as system environment variables (
AWS_ACCESS_KEY_IDandAWS_SECRET_ACCESS_KEY), or in the default credential profiles file (typically something like~/.aws/credentials). You may also configure the credentials explicitly across the entire Data Management site or on a user-by-user basis.
You must have Administrator privileges to do this.
Once access to S3 resources is configured, any Data Management browse dialog that supports DFS paths will display a file system labeled S3 Buckets at the root level of the browse window. Expand that item to display a list of all Buckets accessible via the configured AWS credentials.
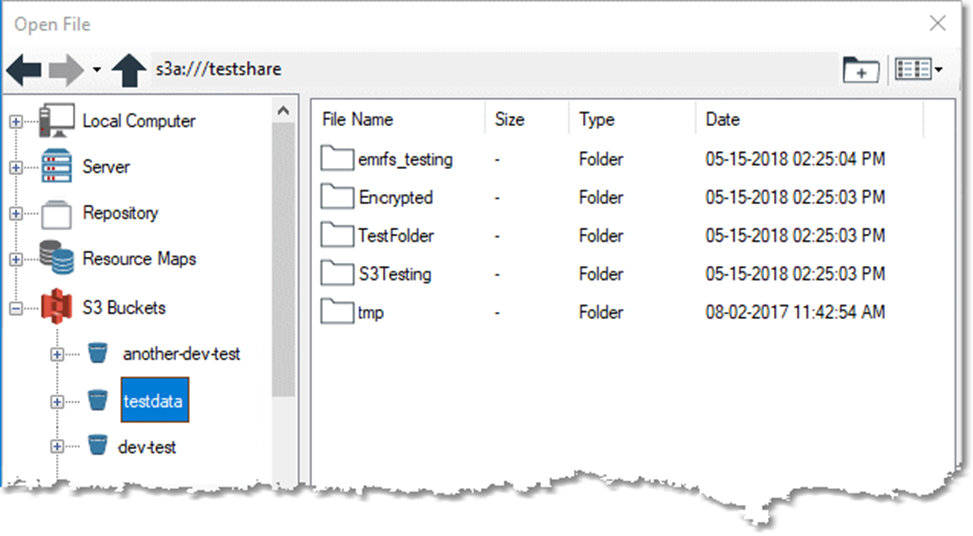
S3 has no append operation. Enabling the Append to existing file option in a Flat File Output tool or a CSV Output tool will result in an error.
Accessing S3 buckets owned by another user
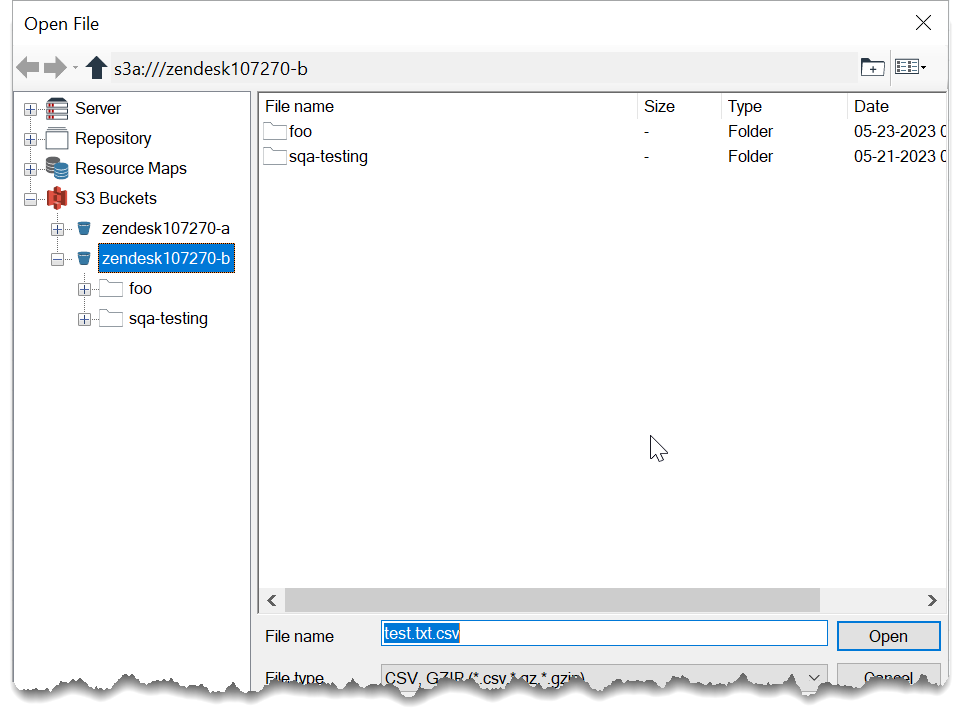
Cross-account buckets are not listed in the File Browser's S3 Bucket file system. To access a cross-account bucket, you must know the bucket name and enter it when configuring tools, steps, or macros.
-
Add a tool to your canvas that you want to access another user's bucket.
-
Open the Properties panel of the tool.
-
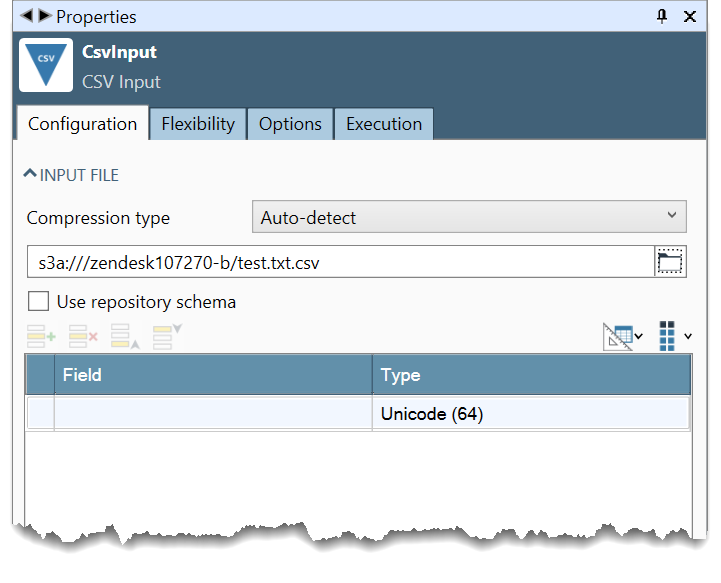
Enter the URI of the bucket you want to access in the File Browser field.
-
Select the Browse button. You will see both your priority bucket and the entered bucket.
Configure access to S3 buckets
To configure site-level access to S3 buckets
-
In the repository, open the Settings folder.
-
Open the Cloud folder.
-
Select the AWS icon.
-
Go to the Properties pane.

-
On the S3 Settings tab, select Expose buckets.
-
If you are not authenticating automatically (via bucket policies or default credential provider chain), open the Authentication section and enter one or more Access key and Secret key pairs. (The Secret key may be a Password or Key Vault reference.) If you have multiple sets of credentials, enter the Access key and Secret key pairs in order of their priority. The first set of credentials with access to a bucket will be used.
You must have Administrator privileges to do this.
-
Optionally, select Encryption type and configure client-side S3 encryption.
To configure user-level access to S3 buckets
-
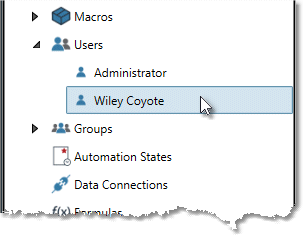
In the repository, open the Users folder and select the desired user.
-
On the User tab of the Properties pane, find the AWS/S3 access section, and then enter the Access key and Secret access key (which may be a Password or Key Vault reference). If Access key and Secret access key pairs are also defined at the site level, these user-level credentials will have priority.
You must have Administrator privileges to do this.
-
Optionally, select Encryption type and configure client-side S3 encryption.
To configure cross-account access to S3 buckets
If no keys are configured, Data Management will attempt to authenticate using the AWS Default Credential Provider Chain.
v9.4.6 - v9.5.3 Beginning in version 9.4.6, Data Management can access buckets owned by another AWS account if IAM policies are properly configured. When attempting to access a cross-account bucket, Data Management will use the first pair of Access keys and Secret keys configured in S3 Settings. Follow the steps in the To configure site-level access to S3 buckets section, and add multiple Access keys and Secret keys in the order of priority, placing the bucket you wish to access first.
new in 9.6.1 In v9.6.1 and later, Data Management can authenticate cross-account bucket access using multiple access/secret key pairs. Even when a bucket is configured to allow cross-account access, it’s not unusual for the owning account to deny external IAM entities “list buckets” permissions. In such cases, the bucket name must be known in advanced and specified manually when building an S3 URI. For convenience, Data Management optionally allows these bucket names to be enumerated in the Unlisted buckets grid associated with each key pair. This results in each defined bucket being shown in the File Browse dialog’s S3 Buckets filesystem.
Cross-account bucket access for multiple accounts is only supported when Access/Secret keys are configured in Settings > Cloud > AWS > Authentication; this use case is not supported when authenticating via an IAM role attached to an EC2 instance profile.
Configure client-side S3 encryption
S3 client-side encryption has been deprecated and will be removed in an upcoming release.
until 9.7.1 AWS S3 supports both server-side (at rest) and client side (in transit) data encryption. Server-side encryption is managed entirely by AWS, and requires no Data Management configuration. If you need to encrypt data before transmitting it to or from AWS S3, you must configure client-side encryption in Data Management.
To configure client-side S3 encryption
-
Select Encryption type and select your desired encryption strategy using the table below.
|
Field |
Description |
|---|---|
|
KMS |
AWS KMS-managed Customer Master key. You must enter the AWS KMS customer master key ID (CMK ID) from AWS. The credentials you used to authenticate above, will also need rights to use that key. |
|
Symmetric key
|
256-bit AES key. Using openssl from a bash shell (Git Bash for example), run the following commands to create a private/public key pair in a directory named Bash
|
|
Public/Private key pair
|
1024-bit RSA key pair. Using openssl from a bash shell (Git Bash for example), run the following commands to create a private/public key pair in a directory named Bash
|

